In the second instalment of a three-part series, BIM Academy technologist Murillo Piazzi gives an overview of the sensitivity assessment and the security management plan stages of ISO 19650-5.
Advances in technology have reduced the cost to produce information models that replicate the conditions of the real world and can be digitally connected to the environment through the Internet of Things.
These advances are part of a bigger landscape of digital innovation, including the use of BIM, and have been transforming the construction industry, facilitating information sharing and visualisation. However, while these technologies facilitate efficiency and quality improvements across uncountable tasks, they also increase the vulnerability of the information.
In my previous article, we saw how ISO 19650-5 is structured to address this challenge. The standard could be split into four main parts. The first, the sensitivity assessment stage, is being mandated in the Infrastructure & Projects Authority’s (IPA) 2030 Roadmap. In this second article of my three-part series on ISO 19650-5, I am going to give an overview of the sensitivity assessment and the initial stage of the security-minded approach – the security management plan.
The sensitivity assessment process
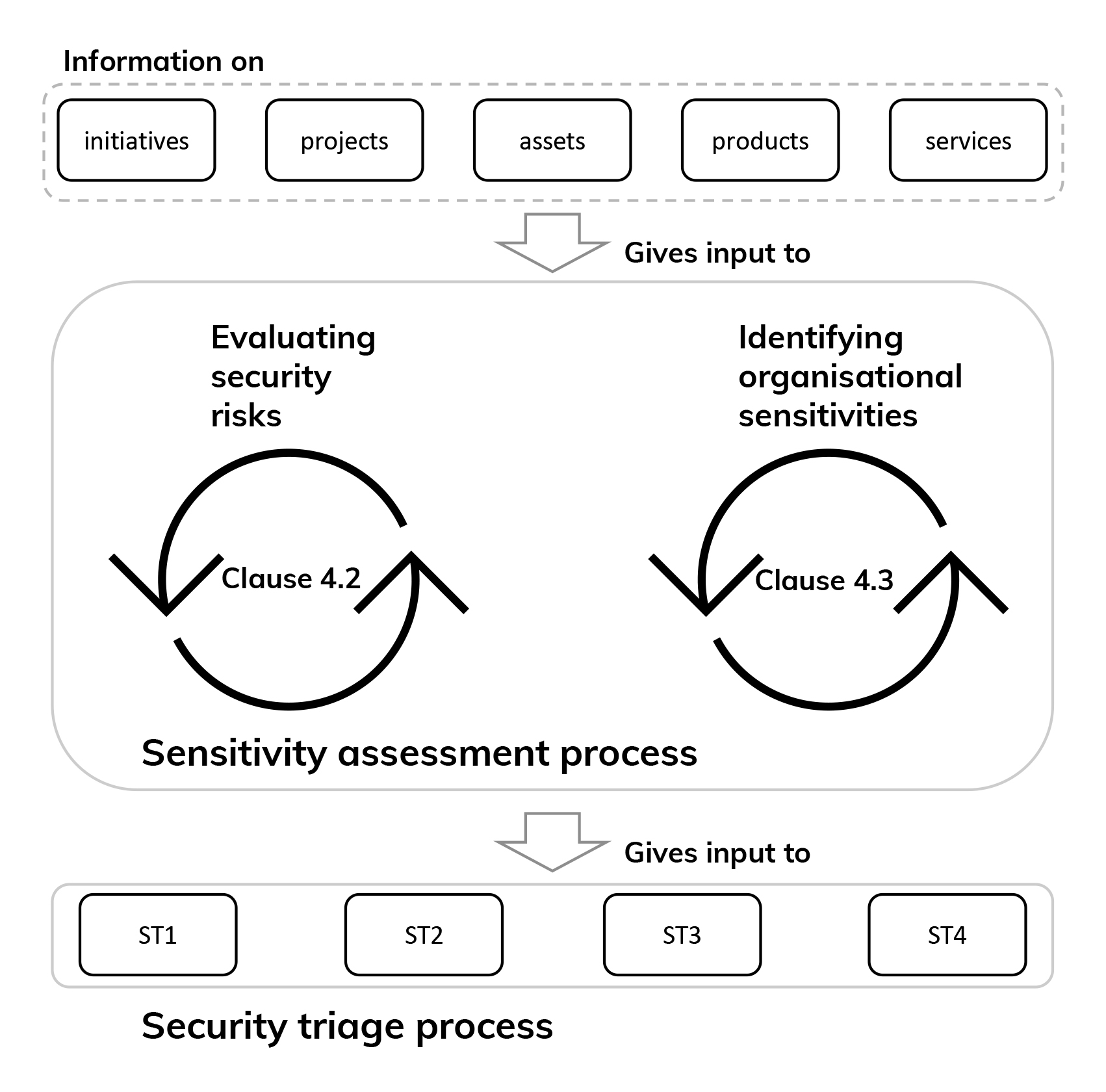
In the sensitivity assessment stage, we are trying to define whether we really need to implement a security-minded approach to secure the information in our project. The main outcome of this process is the creation of a document containing the findings of what ISO calls ‘the security triage process’.
The responsibility for initiating this process lies with the top management of organisations who own/will own the asset. Moreover, if more than one organisation (e.g. multiple clients) is involved on a project, they need to coordinate their actions to contribute towards the assessment process.

“One of the biggest values in this process lies in the structured approach to prioritisation of information’s sensitivity.”
The sensitivity assessment process involves two main tasks. First, evaluation of the security risks: the security triage process starts with an evaluation of the security risks that can be applied to the building and civil engineering-related information under the responsibility of the organisation.
A list of risk examples is given in Annex A of the ISO standard. For example, one of the suggestions is to review the potential for existing systems to grant unauthorised access to information. Projects that implement a simple directory-based folder structure on the organisation’s extranet with open permissions to store data, would be a prime example of the risks that should be identified as part of this.
Second, identification of organisational sensitivities: this involves checking whether information gathered/to be gathered falls within the criteria described in ISO 19650-5 and, consequently, whether it should be considered sensitive or not. Those responsible for this task should take the risks found in the previous step into consideration and evaluate them from various perspectives.
For example, the assessment suggested by the standard is not restricted to risks to the distribution of information on physical building elements. It also considers products, services, technologies, resources, etc. Details about the maintenance regime, for example, could be used to inform perpetrators about vulnerable periods in the security systems (e.g. CCTV, access control).
When people start thinking about security, a common mistake is to want to make all information on a project secure. Doing so could become a very onerous task. Therefore, one of the biggest values in this process lies in the structured approach to prioritisation of information’s sensitivity, so that appropriate and proportionate security measures can be put in place.
Developing a security strategy
Based on the outcome of the security triage process, you should be able to determine whether a security-minded approach is required. If so, the organisation could define a strategy for protecting sensitive information in a document called the “security strategy”.
However, the development of the security-minded approach should be preceded by the establishment of a governance, accountability and responsibility framework. This stage could be thought of as a series of housekeeping tasks that should be carried out across organisations so that they can agree on how effort is going to be apportioned and determine accountability and responsibility for the processes moving forward.
After this initial set-up of responsibilities, organisations are ready to start working on the security strategy. There are two main goals here. First, we need to assess the security risks that arise from the fact that the data on the project is digitised and more accessible to people. Second, we need to agree on the possible actions for mitigating these risks.
Security risks identified in the previous stage, the sensitivity assessment process, should be reviewed to consider the potential threats and vulnerabilities. For example, what threats could arise if the layout of a police station is widely shared with the public?
The nature of the risk should then be reviewed as to its impact were this information to be leaked. Could it be used to support hostile reconnaissance of a building? Will it make assets and people vulnerable to an attack? Finally, the probability of these risks materialising should be identified.
Once these threats and vulnerabilities are analysed, the process then moves on to the definition of mitigation measures. The standard recommends for us to assess the security measures we are planning to establish across a number of key factors – implementation costs, risk reduction levels, predicted impacts and business benefits should all be considered. This will help the organisation to determine an appropriate approach to mitigation.
Initially, many pieces of information might be regarded as sensitive on construction projects – the properties of security systems, the location of strategic infrastructure and assets, etc. However, organisations might find that not all of them will need to be secured – the risks associated with the details of how a publicly visible CCTV system work in a rural police station are different from the risks of how a similar system works in a museum, where millions of pounds worth of art is stored.
Different contexts will have an impact on how risks and mitigation measures are perceived along with which have a higher priority for implementation.
After going through these two initial assessments, you should have a comprehensive understanding of the sensitivities and the range of security risks in your organisation as well as associated mitigation measures.
The focus of the security measures should be narrowed down to only key sensitive pieces of information. The processes and tasks to effectively protect them will be specified in the security management plan and appointment documents, and this is what I will investigate in my next article.
Don’t miss out on BIM and digital construction news: sign up to receive the BIMplus newsletter.